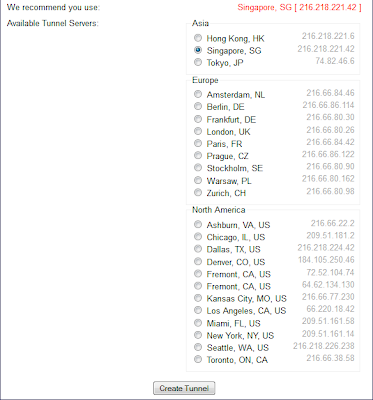
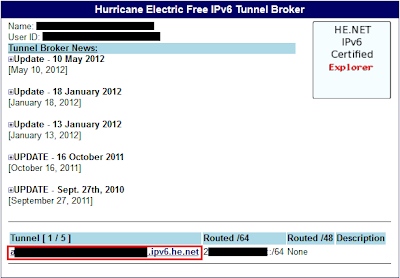
It has been a while since I have written anything, but if you notice I have been updating the OpenWRT Attitude Adjustment Builds on TP-Link WR1043ND.
I have removed a lot of excess packages since so you can actually install the stuff you want. You can do extroot if there is still not enough.
Upgrading the firmware is actually a piece of cake, I do it in 5 minutes.
1) Make sure the backup utility in openwrt backs up the configuration you want.
2) Create archive using the backup utility
3) Flash and clear settings
4) Log in to router update time and disable unwanted startups
5) Upload the backup archive. Done!
Cheers.
I have removed a lot of excess packages since so you can actually install the stuff you want. You can do extroot if there is still not enough.
Upgrading the firmware is actually a piece of cake, I do it in 5 minutes.
1) Make sure the backup utility in openwrt backs up the configuration you want.
2) Create archive using the backup utility
3) Flash and clear settings
4) Log in to router update time and disable unwanted startups
5) Upload the backup archive. Done!
Cheers.